Hidpss Are Also Known As System Integrity Verifiers
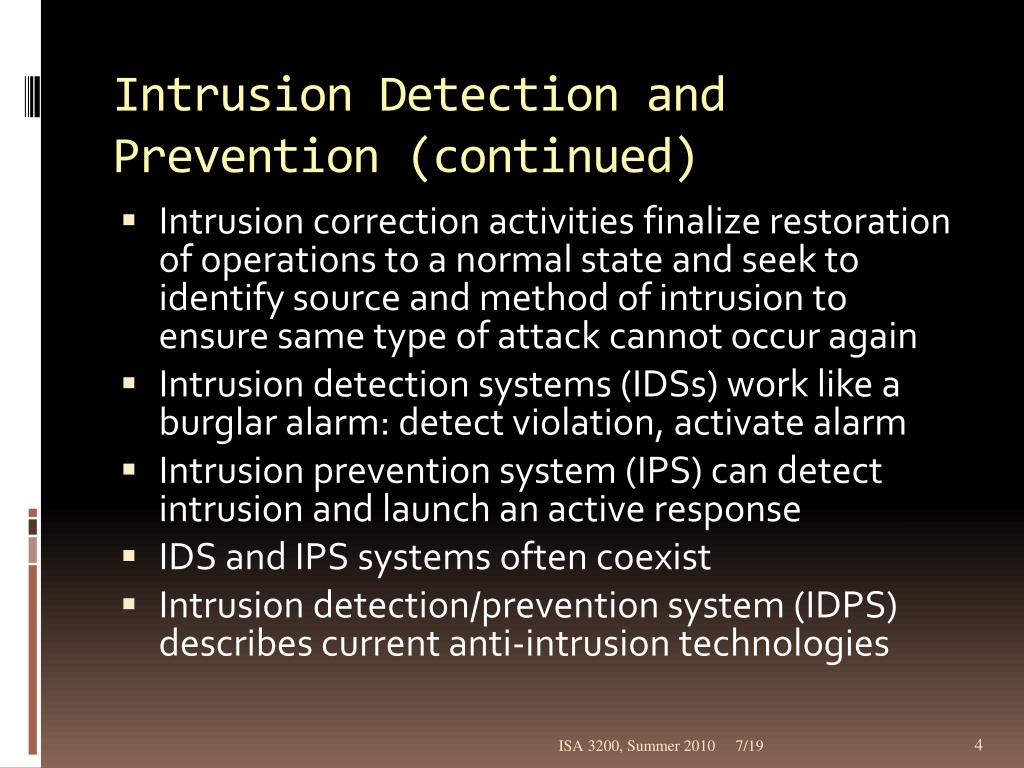
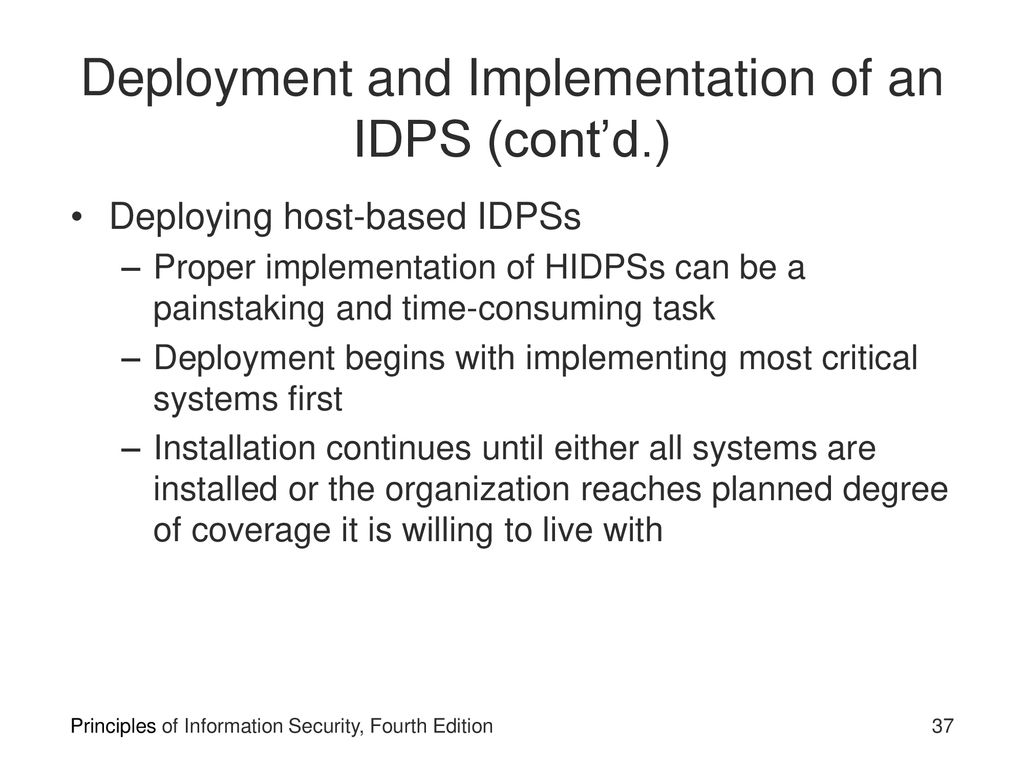
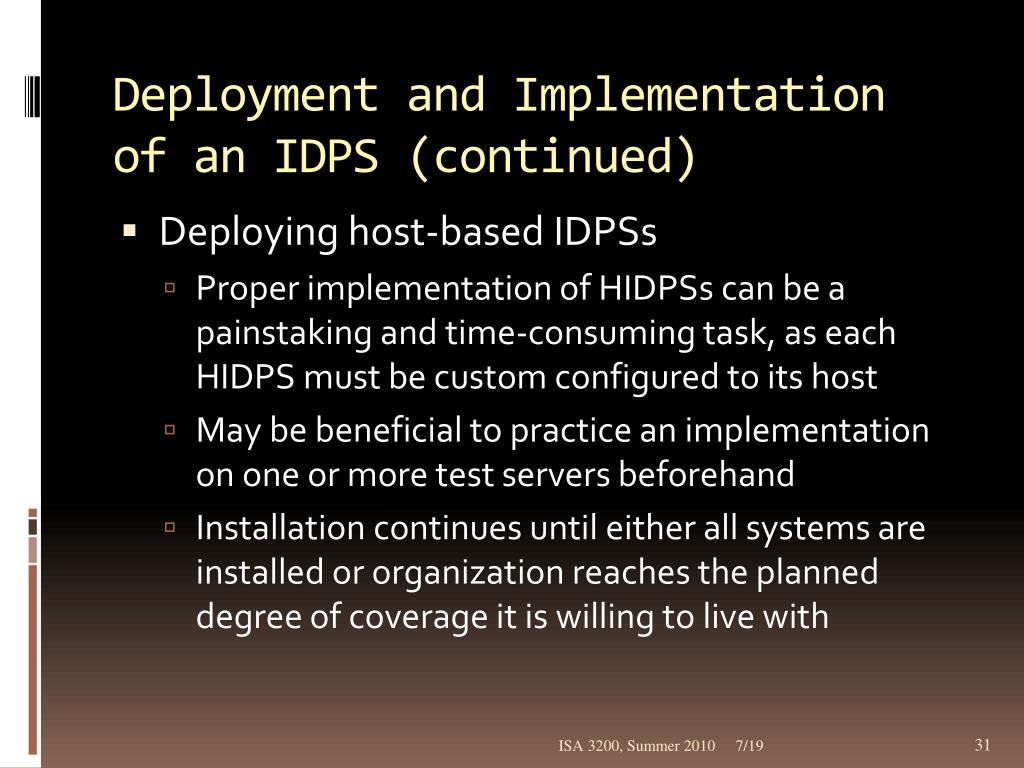
Hidpss are also known as system integrity verifiers. CorrectMarks for this submission. The database contains a copy of the file systems partition table referencing the range of occupied. Intrusion detection consists of procedures and systems that identify system intrusions and take action when an intrusion is detected.
Ερώτηση 1 of 1 Υπολειπόμενος Χρόνος Παράλειψη Ερώτησης Αποκαλύψτε Τις Απαντήσεις Παίξτε Την Επόμενη Ερώτηση. All of the above. Παίζω ITS 221 ch7-9.
HIDSs are also known as system integrity verifiers. Asked Mar 9 2017 in Trades Technology by Wutwut. HIDPSs are also known as system integrity verifiers.
HIDPSs are also known as system _____ verifiers. HIDPSs are also known as system integrity verifiers. An HIDPS has an advantage over an NIDPS in that it can access encrypted information traveling over the network and use it to make decisions about potential or actual attacks.
In public key encryption for authentication the verifier decrypts the ciphertext with the verifiers public key. 2 A false positive is the failure of an IDPS system to react to an actual attack eventAnswer. Most HIDPSs work on the principle of configuration or change management they record the.
An intrusion detection system IDS is a tool or software that works with your network to keep it secure and flag when somebody is trying to break into your system. A LEED for Homes B National Green Building Standard C EarthCraft D ENERGY STAR. Active Systems And Falsea N.
HIDPSs are also known as system _____ verifiers. Active Vulnerability Scanner A n active vulnerability scanner is one that initiates traffic on the network in order to determine security.
Can include variables such as host memory or CPU.
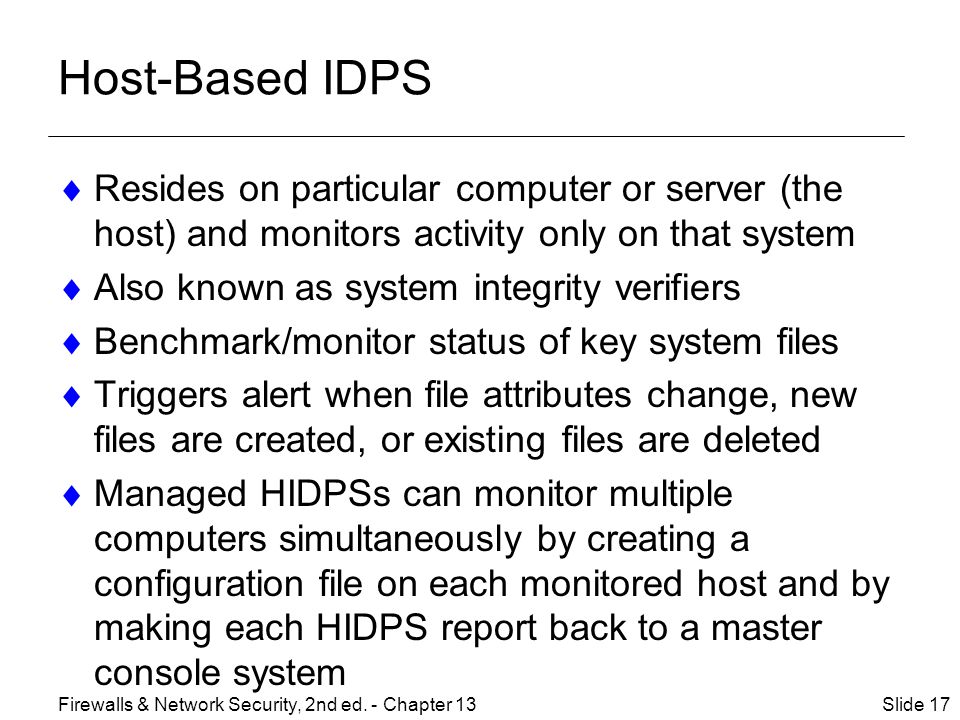
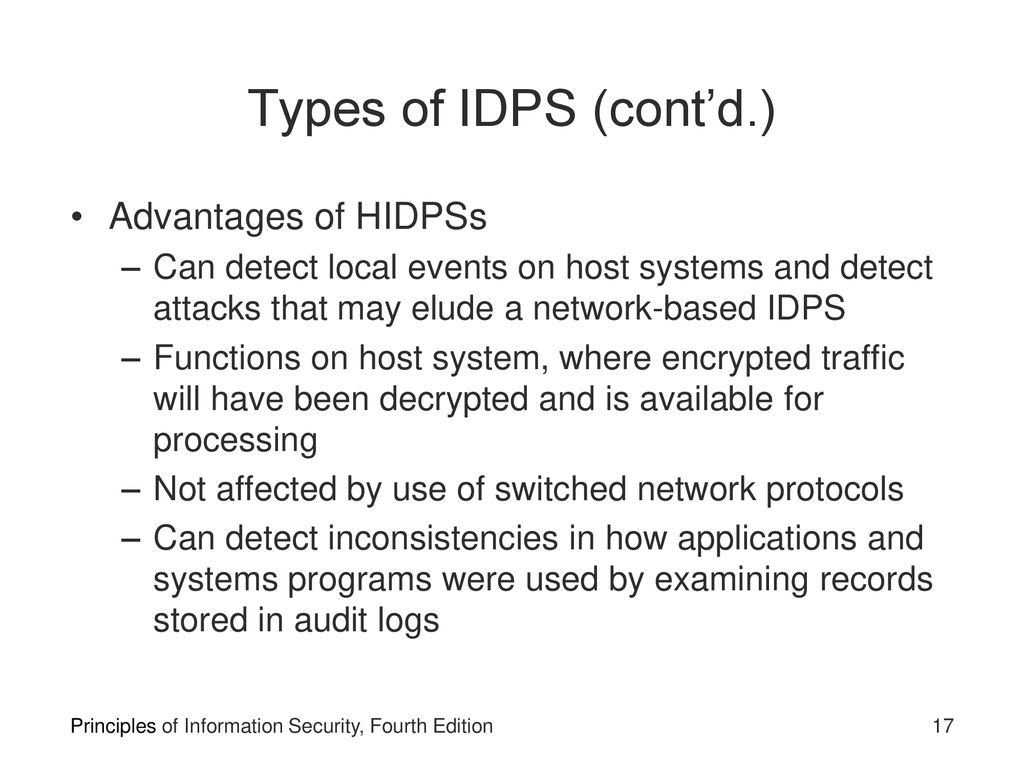
An HIDPS can detect local events on host systems and also detect attacks that may elude a network-based IDPS. HIDSs are also known as system integrity verifiers. In this ultimate guide Ill go through everything you. Bermain ITS 221 ch7-9. HIDPSs are also known as system integrity verifiers because they benchmark and monitor the status of key system files and detect when an intruder creates modifies or deletes monitored files. All of the above. Ερώτηση 1 of 1 Υπολειπόμενος Χρόνος Παράλειψη Ερώτησης Αποκαλύψτε Τις Απαντήσεις Παίξτε Την Επόμενη Ερώτηση. An intrusion detection system IDS is a tool or software that works with your network to keep it secure and flag when somebody is trying to break into your system. Because they assess and monitor the status of critical system files and identify when an attacker creates updates or deletes observed files HIDPSs are also referred to as system integrity verifiers.
Iris of the eye d. True ____ are usually passive devices and can be deployed into existing networks with little or no disruption to normal network operations. Bermain ITS 221 ch7-9. Asked Mar 9 2017 in Trades Technology by Wutwut. Also known as system integrity verifiers Benchmarkmonitor status of key system files Triggers alert when file attributes change new files are created or existing files are deleted Managed HIDPSs can monitor multiple computers simultaneously by creating a configuration file on each monitored host and by. STATISTICAL ANOMALY-BASED IDPS The statistical anomaly-based IDPS stat IDPS or behavior-based IDPS sample network activity to compare to traffic that is known to be normal When measured activity is outside baseline parameters or clipping level IDPS will trigger an alert data is measured from the normal traffic then it is used to prepare the baseline. An HIDPS has an advantage over an NIDPS in that it can access encrypted information traveling over the network and use it to make decisions about potential or actual attacks.






























Post a Comment for "Hidpss Are Also Known As System Integrity Verifiers"